I'm re-enabling AFL since the issue with gmock's main being present was fixed in
|
||
|---|---|---|
| docs | ||
| infra | ||
| projects | ||
| .gitignore | ||
| .travis.yml | ||
| CONTRIBUTING | ||
| LICENSE | ||
| README.md | ||
| oss-fuzz.iml | ||
README.md
OSS-Fuzz: Continuous Fuzzing for Open Source Software
Fuzz testing is a well-known technique for uncovering programming errors in software. Many of these detectable errors, like buffer overflow, can have serious security implications. Google has found thousands of security vulnerabilities and stability bugs by deploying guided in-process fuzzing of Chrome components, and we now want to share that service with the open source community.
In cooperation with the Core Infrastructure Initiative, OSS-Fuzz aims to make common open source software more secure and stable by combining modern fuzzing techniques with scalable, distributed execution.
We support the libFuzzer and AFL fuzzing engines in combination with Sanitizers, as well as ClusterFuzz, a distributed fuzzer execution environment and reporting tool.
Currently, OSS-Fuzz supports C/C++, Rust, and Go code. Other languages supported by LLVM may work too. OSS-Fuzz supports fuzzing x86_64 and i386 builds.
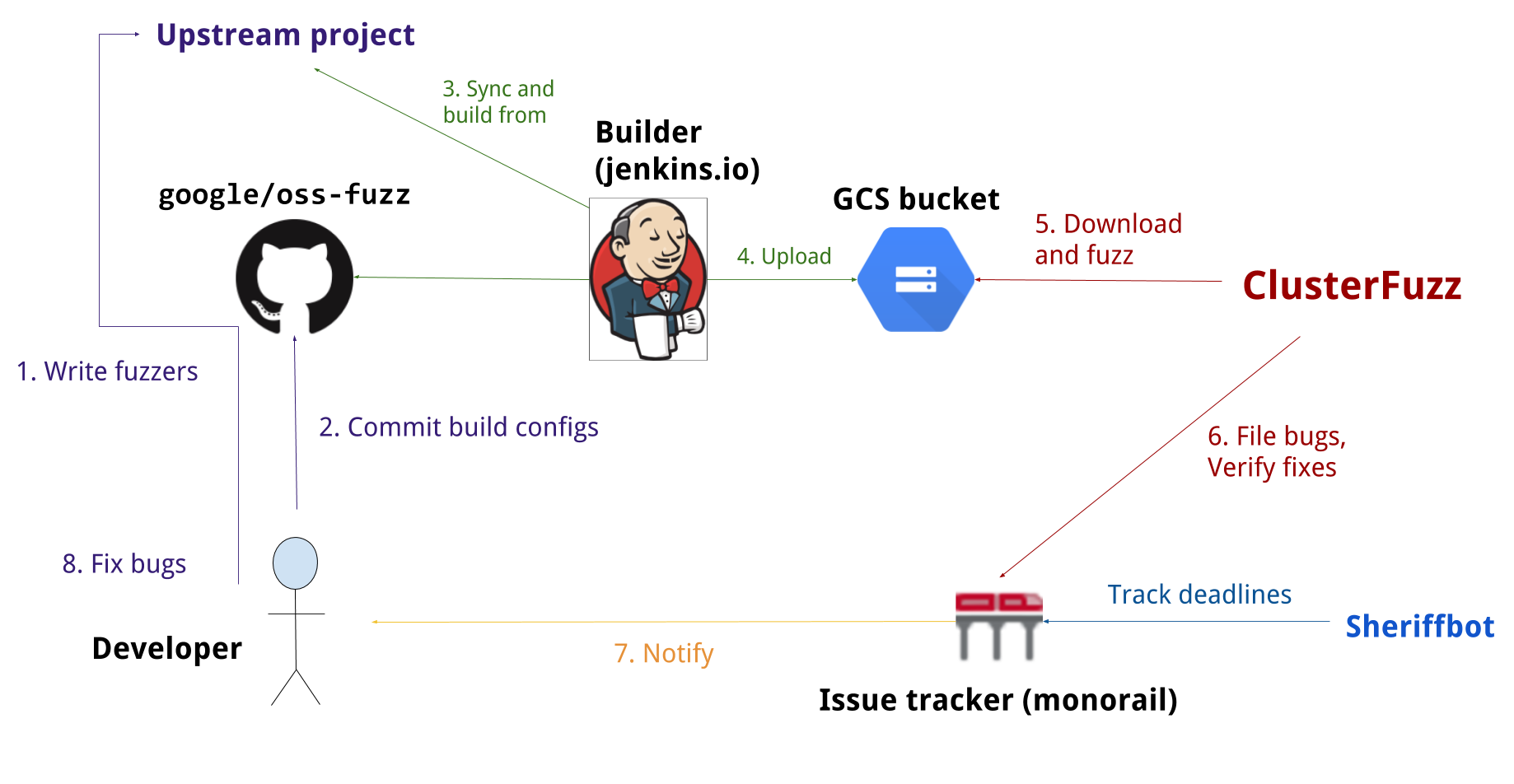
Overview
Documentation
Read our detailed documentation to learn how to use OSS-Fuzz.
Trophies
As of August 2019, OSS-Fuzz has found over 14,000 bugs in 200 open source projects.
Blog posts
- 2016-12-01 - Announcing OSS-Fuzz: Continuous fuzzing for open source software
- 2017-05-08 - OSS-Fuzz: Five months later, and rewarding projects
- 2018-11-06 - A New Chapter for OSS-Fuzz