* Add new fuzz target for encoding and misc - Add fuzz_webp_enc_dec and adapt Dockerfile, build.sh - Lint existing targets - Add license headers - Increase fuzz.dict * webp_enc_dec: Convert input images to inline C arrays Local files are not available on oss-fuzz servers. * webp_enc_dec: Fix timeout by skipping crusher The target fuzz_webp_enc_dec with msan crashes (timeout) on a 128*128px image encoding with max compression (crusher). Reduce crusher encoding to 16*16px and below. Bug report 10423 * webp_enc_dec: Replace cruncher by lossy alpha encoding The target fuzz_webp_enc_dec with msan crashes (timeout) during encoding with max compression (cruncher). Reduce alpha cruncher encoding to 16*16px and below. Bug report 10634 * webp_enc_dec: Clamp slow parameters for big images The target fuzz_webp_enc_dec with ubsan crashes (timeout) during encoding with heavy compression. The cause can not be easily removed without reducing performance. Clamp compression parameters for images bigger than 16*16. Bug report 10700 * webp_enc_dec: Limit alpha_quality to 99 when method is 6 The target fuzz_webp_enc_dec with asan crashes (timeout) during encoding with heavy alpha compression. Clamp alpha compression parameters for images bigger than 16*16. Bug report 10838 * webp_animencoder: Add target to fuzz animation encoding Add fuzz_webp_animencoder.cc and modify Dockerfile, build.sh accordingly. The thresholds for input size and encoding parameters are low to prevent timeouts. Some functions used by fuzz_webp_animencoder and fuzz_webp_enc_dec have been moved to fuzz.h. |
||
|---|---|---|
| docs | ||
| infra | ||
| projects | ||
| .gitignore | ||
| CONTRIBUTING | ||
| LICENSE | ||
| README.md | ||
README.md
OSS-Fuzz - Continuous Fuzzing for Open Source Software
Status: Stable. We are accepting applications from widely-used open source projects.
FAQ | Ideal Fuzzing Integration | New Project Guide | Reproducing Bugs | Projects | Projects Issue Tracker | Glossary
Create New Issue for questions or feedback about OSS-Fuzz.
Introduction
Fuzz testing is a well-known technique for uncovering various kinds of programming errors in software. Many of these detectable errors (e.g. buffer overflow) can have serious security implications.
We successfully deployed guided in-process fuzzing of Chrome components and found hundreds of security vulnerabilities and stability bugs. We now want to share the experience and the service with the open source community.
In cooperation with the Core Infrastructure Initiative, OSS-Fuzz aims to make common open source software more secure and stable by combining modern fuzzing techniques and scalable distributed execution.
At the first stage of the project we use libFuzzer with Sanitizers. More fuzzing engines will be added later. ClusterFuzz provides a distributed fuzzer execution environment and reporting.
Currently OSS-Fuzz supports C and C++ code (other languages supported by LLVM may work too).
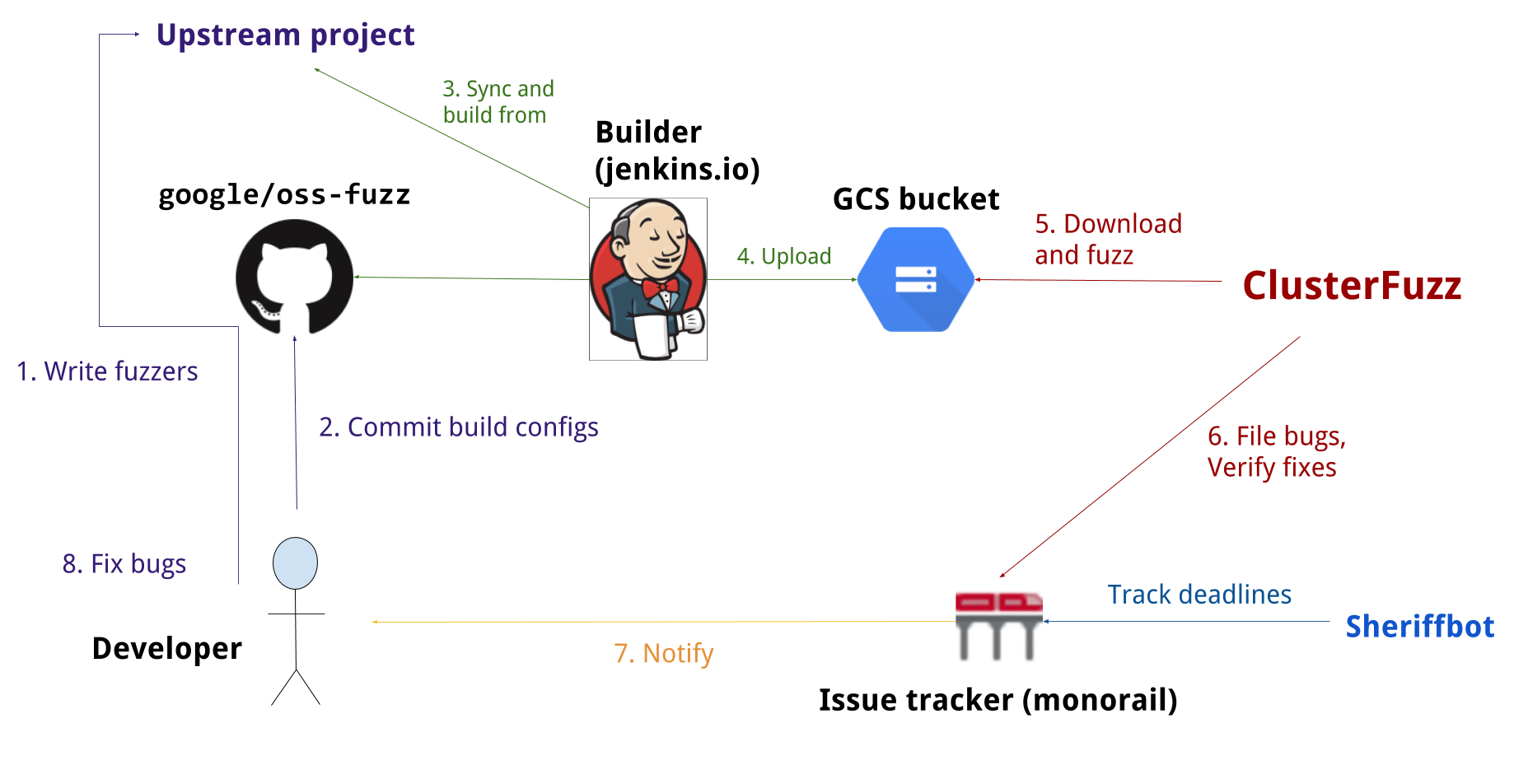
Process Overview
The following process is used for projects in OSS-Fuzz:
- A maintainer of an opensource project or an outside volunteer creates one or more fuzz targets and integrates them with the project's build and test system.
- The project is accepted to OSS-Fuzz.
- When ClusterFuzz finds a bug, an issue is automatically reported in the OSS-Fuzz issue tracker (example). (Why use a different tracker?). Project owners are CC-ed to the bug report.
- The project developer fixes the bug upstream and credits OSS-Fuzz for the discovery (commit message should contain the string 'Credit to OSS-Fuzz').
- ClusterFuzz automatically verifies the fix, adds a comment and closes the issue (example).
- 30 days after the fix is verified or 90 days after reporting (whichever is earlier), the issue becomes public (guidelines).
Accepting New Projects
To be accepted to OSS-Fuzz, an open-source project must have a significant user base and/or be critical to the global IT infrastructure. To submit a new project:
- Create a pull request with new
projects/<project_name>/project.yamlfile (example) giving at least the following information:- project homepage.
- e-mail of the engineering contact person to be CCed on new issues. It should:
- belong to an established project committer (according to VCS logs). If this is not you or the email address differs from VCS, an informal e-mail verification will be required.
- be associated with a Google account (why?). If you use an alternate email address linked to a Google Account, it will ONLY give you access to filed bugs in issue tracker and NOT to ClusterFuzz dashboard (due to appengine api limitations).
- Note that
project_namecan only contain alphanumeric characters, underscores(_) or dashes(-).
- Once accepted by an OSS-Fuzz project member, follow the New Project Guide to configure your project.
Bug Disclosure Guidelines
Following Google's standard disclosure policy OSS-Fuzz will adhere to following disclosure principles:
- Deadline. After notifying project authors, we will open reported issues to the public in 90 days, or 30 days after the fix is released (whichever comes earlier).
- Weekends and holidays. If a deadline is due to expire on a weekend, the deadline will be moved to the next normal work day.
- Grace period. We have a 14-day grace period. If a 90-day deadline expires but the upstream engineers let us know before the deadline that a patch is scheduled for release on a specific day within 14 days following the deadline, the public disclosure will be delayed until the availability of the patch.
More Documentation
- Glossary describes the common terms used in OSS-Fuzz.
- New Project Guide walks through the steps necessary to add new projects to OSS-Fuzz.
- Ideal Integration describes the steps to integrate fuzz targets with your project.
- Accessing corpora describes how to access the corpora we use for fuzzing.
- Fuzzer execution environment documents the environment under which your fuzzers will be run.
- Projects lists OSS projects currently analyzed by OSS-Fuzz.
- Chrome's Efficient Fuzzer Guide while containing some Chrome-specific bits, is an excellent guide to making your fuzzer better.
- Blog posts:
Build Status
This page gives the latest build logs for each project.
(Internal only) Builds dashboard.
Trophies
This page gives a list of publicly-viewable fixed bugs found by OSS-Fuzz.